|
Secure Image Coding
|

Input image |
Encryption schemes based on visual cryptography principles are designed
to ensure the confidentiality of binary or binarized images. To take
into account the special properties of gray-scale and color images, an
image secret sharing framework with perfect reconstruction of the secret
image has been introduced. However, such solutions may not be suitable
when transmitting large still images and video via public wireless and
mobile networks, as the visual material can be overwhelming to transmit
due to its large size necessitating the use of complex compression
algorithms. |
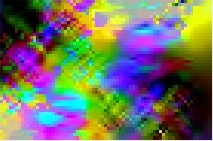
Image decoded without
key |
|
Efficiently encrypting still color images is usually
based on the principle of partial or selective encryption and relies
on the compression algorithm, for example color set partitioning in
hierarchical trees compression, in order to produce a secure coded
image. It directs a stream cipher to encrypt only certain
significance bits, resulting thus in minimal computational overhead.
To unaffect the rate-distortion performance of the compression
algorithm, specific bits of the image should be encrypted after
encoding. Both efficiency and confidentiality of the approach is
ensured by encrypting only the significance bits of individual
coefficients and determining how many coding iterations for which
the encryption should be performed. The confidentiality of the image
also results from the unknown arrangement of encrypted and
unencrypted bits. The principles behind the presented solution may
be applied to various embedded image and video coders. |
|
References: |
|
 |
R. Lukac and K.N. Plataniotis, Secure Color Imaging. In Color
Image Processing: Methods and Applications, (eds.) R. Lukac and K.N.
Plataniotis, CRC Press / Taylor & Francis, pp. 185-202, October 2006.
ISBN 0-8493-9774-X |
 | K. Martin, R. Lukac and K.N. Plataniotis, "Efficient Encryption of Wavelet-Based Coded Color Images," Pattern Recognition, vol. 38, no. 7, pp. 1111-1115, July 2005. |
|
|
|
